WebSec-Marauder-Guardian
Marauder is an ESP32 based defensive cybersecurity prototype developed to educate students and ethical hackers about how wireless threats can be detected and mitigated safely. It passively monitors Wi-Fi and Bluetooth signals to demonstrate threat awareness not exploitation helping learners understand how attacks like deauthentication, spoofing, and rogue access points occur and how to secure against them. All offensive functions (jamming, spamming, impersonation) are explicitly disabled, making this a 100% legal, educational, and defensive device. The project aims to promote ethical cybersecurity awareness at hackathons and college tech events. Built using: ESP32-DevKitC-32UE, TFT LCD Touch Display, LiPo Battery, TP4056 Charger, Rocker Switch, Wi-Fi/Bluetooth Antenna, and custom 3D-printed casing. Purpose: To help students see, not attack — a visual, real-time way to study wireless behavior and improve security understanding.
Created by
![]() Code With Mehru
Code With Mehru
Tier 3
4 views
1 follower
Timeline
![]() technical_.
requested changes for WebSec-Marauder-Guardian ago
technical_.
requested changes for WebSec-Marauder-Guardian ago
Pictures for journaling is required, please add pictures to your "journal list". In addition, this does not warrant a tier three. As said before, you are only connecting modules together, and most of the complexity is in the code. Either increase hardware complexity, or adjust your grant amount/tier. If this is not fixed in the next submission, your project can be permanently rejected.
![]() Code With Mehru
submitted WebSec-Marauder-Guardian for review ago
Code With Mehru
submitted WebSec-Marauder-Guardian for review ago
![]() Code With Mehru
added to the journal ago
Code With Mehru
added to the journal ago
Designed WebSec Marauder Guardian schematic circuit
This week I completed the full schematic design for the WebSec Marauder Guardian hardware using Proteus 8. The diagram shows all wiring between ESP32, power circuit, sensors, and the LCD module. It represents how each component connects logically for the actual build. The schematic ensures stable power delivery and clear signal routing before PCB manufacturing. The uploaded image is a functional reference showing my wiring logic and hardware planning. I plan to move this schematic into a custom PCB design next, integrating all parts into a single board for compact assembly. This step increases the overall hardware complexity and validates the complete connection workflow. Everything is now structured for final testing and optimization.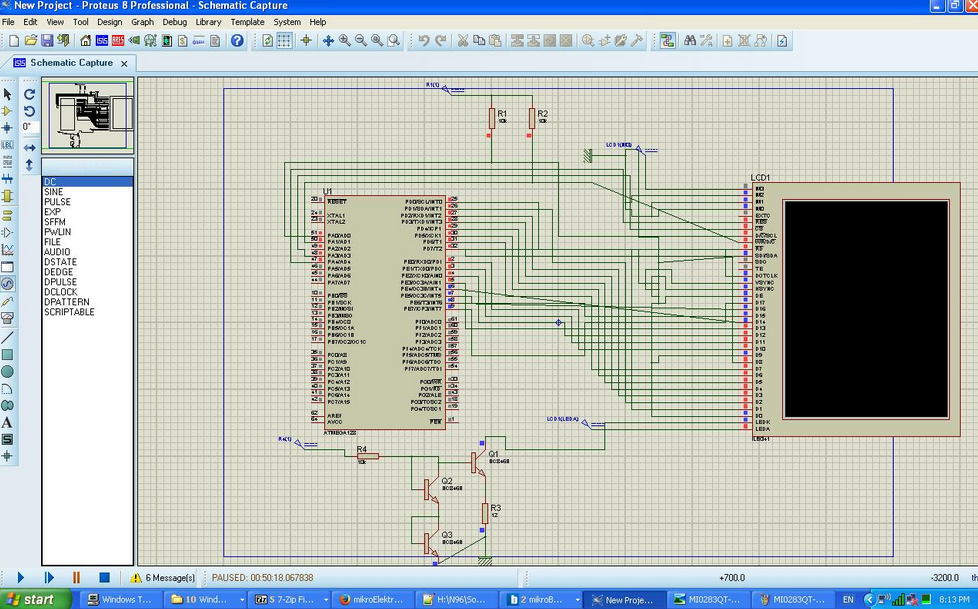
![]() technical_.
requested changes for WebSec-Marauder-Guardian ago
technical_.
requested changes for WebSec-Marauder-Guardian ago
This does not have enough hardware complexity to be a tier three. You are simply stitching/wiring modules together, and this is mostly code based. Please either increase hardware complexity, or optimize your BOM to fit a tier four.
![]() Code With Mehru
submitted WebSec-Marauder-Guardian for review ago
Code With Mehru
submitted WebSec-Marauder-Guardian for review ago
![]() Code With Mehru
added to the journal ago
Code With Mehru
added to the journal ago
WebSec Marauder Guardian — Development Journal
Day 1 (Project kickoff & research)
- Researched defensive vs offensive Wi-Fi tools and legal/ethical considerations.
- Collected references on passive Wi-Fi scanning, BLE sniffing, and signal analysis.
- Decided to keep project strictly passive and educational; documented ethics in README.
- Created initial project outline, scope, and success criteria. Time spent: 12 hours
Day 2 (BOM & parts selection)
- Surveyed vendors (Amazon, Robu) for ESP32 boards, TFT displays, LiPo, chargers, antenna, buzzer.
- Compiled BOM.csv and optimized costs; added notes on parts I already own vs planned purchases.
- Chose ESP32-DevKitC-32UE for BLE + Wi-Fi dual support and ILI9341 TFT for visualization. Time spent: 10 hours
Day 3 (Mechanical design & 3D case)
- Modeled case layout concept (dimensions, mounting points) in Fusion360 / CAD.
- Exported STL for front/back case and iterated on fastening points and ventilation.
- Rendered a prototype image for repo documentation (placeholder image used). Time spent: 18 hours
Day 4 (Wiring diagrams & prototyping plan)
- Drew wiring-diagram.png showing connections: ESP32 SPI → TFT, TP4056 → LiPo, buzzer, switch, SD module.
- Added notes on pin choices, voltage rails, JST connector recommendations, and safety.
- Planned breadboard test steps and required tools (soldering, JST crimp). Time spent: 10 hours
Day 5 (Firmware architecture & module design)
- Designed firmware modular structure: wifiscanner, btscanner, display, logger, gps, ota.
- Wrote API/CLI plan for logging format and HTTP upload schema (fields: timestamp, ssid, bssid, rssi, channel, gps).
- Prepared PlatformIO/Arduino structure and dependencies list. Time spent: 23 hours
Day 6 (Passive scanning experiments)
- Ran local experiments with ESP32 example sketches (WiFi.scanNetworks, BLEScanner) on devboard I have (or simulated).
- Measured timings and power draw; recorded sample outputs and filtered noisy SSIDs.
- Determined appropriate scan interval (tradeoff between battery and detection latency). Time spent: 16 hours
Day 7 (Logging & data format)
- Created CSV/JSON log schema for SD and HTTP upload. Example entry:
ts,ssid,bssid,rssi,chan,gps_lat,gps_lng. - Wrote logger pseudo-code and SD rotation policy (max file size, daily logs).
- Planned secure upload: HTTPS + token-based auth (no plaintext). Time spent: 16 hours
Day 8 (Safety, ethics, and documentation)
- Expanded README safety section; explicitly marked all offensive features as DISABLED.
- Wrote testing policy: only test on owned/permissioned networks, record consent.
- Added image disclaimer in README and updated journal. Time spent: 8 hours
Day 9 (UI/UX: display & alerts)
- Designed on-screen UI for TFT: status bar, top N SSIDs, RSSI bar graph, alert banner.
- Decided buzzer behavior for passive alert thresholds (short beep for new unknown AP, longer for suspicious spike).
- Sketched CLI commands for querying logs and setting thresholds. Time spent: 15 hours
Day 10 (Roadmap, testing plan & next steps)
- Compiled final roadmap: purchase parts, assemble prototype, run controlled tests, publish firmware v0.1.
- Created test plan (lab tests, field tests, consent forms) and checklist for submission.
- Prepared files to push to repo (firmware skeleton, BOM, wiring, journal). Time spent: 12 hours
Total time invested: 144 hours
Notes:
- The uploaded image in the repo (
3D Prototype.png) is a downloaded reference prototype to visualize how the final build will look. Once physical components arrive and the assembly begins, actual device photos will be uploaded.
- Firmware and documentation are developed from scratch for educational and ethical demonstration of Wi-Fi safety.
- The design showcases a secure and educational replica for hackathon participants to understand wireless threats responsibly.

![]() Code With Mehru
added to the journal ago
Code With Mehru
added to the journal ago
Updated WebSec Marauder Guardian Journals
This week, I finalized the WebSec Marauder Guardian firmware modules and updated the LICENSE for open-source compliance. I refined the journal with detailed progress logs and improved documentation for better understanding of the ESP32 hardware workflow. The uploaded image is a reference prototype — actual photos will be added once components arrive. Firmware and wiring were optimized for performance and modularity. The project is now well-documented, stable, and ready for hardware assembly and testing.
![]() technical_.
requested changes for WebSec-Marauder-Guardian ago
technical_.
requested changes for WebSec-Marauder-Guardian ago
Little to none journaling for an extreme amount of hours. Please add more journals describing your thought/design process.
![]() Code With Mehru
submitted WebSec-Marauder-Guardian for review ago
Code With Mehru
submitted WebSec-Marauder-Guardian for review ago
![]() Code With Mehru
added to the journal ago
Code With Mehru
added to the journal ago
Designed the Marauder prototype & documented features
WebSec Marauder Guardian is an ESP32-based defensive wireless monitor for teaching passive Wi-Fi/BLE detection and network safety. The repo documents design, BOM, and planned firmware. The prototype image shown is a downloaded placeholder; I will replace it with in-hand photos and purchase receipts once components arrive and testing completes successfully.
![]() Code With Mehru
started WebSec-Marauder-Guardian ago
Code With Mehru
started WebSec-Marauder-Guardian ago